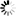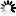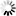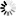FlowTraq uses Traffic Groups to represent the logical makeup of your network in terms of sections of netblocks and/or individual IP addresses. These groupings form the basis of alerting policy for FlowTraq, and for long-term trend analysis, and they also provide a convenient granularity between the netblock and autonomous system level when examining your traffic. The addresses in these groups are independent of the "internal" addresses at the partition level; any individual Traffic Group may contain a mix of internal addresses, or none at all.
Each flow record received by FlowTraq is annotated with one Traffic Group per side of the conversation. When host 10.0.0.1 makes a connection to host 10.0.0.2 on port 443 from some ephemeral port (e.g. 10.0.0.1:34567 → 10.0.0.2:443 (TCP)), FlowTraq looks up each host (and, if appropriate, the port on which the communication took place) and adds an annotation to each address denoting which (if any) Traffic Group it belongs to. (e.g. 10.0.0.1:34567 ["Workstations"] → 10.0.0.2:443 ["My Web Servers"] (TCP)) Each address receives only one such annotation, according to the most specific rule.
Once Traffic Groups are defined, then they will appear on the Policy page immediately and become available for setting policies. Flows must arrive and be matched to a group before statistics for that Traffic Group start to appear on the Quickviews page. Traffic Group definition is not retroactive.
The Traffic Group page can be reached under Adminstration on the top Navigation bar, or linked from the relevant Partition on the Users page. This page permits selecting and editing existing Traffic Groups, as well as the ability to define new ones.
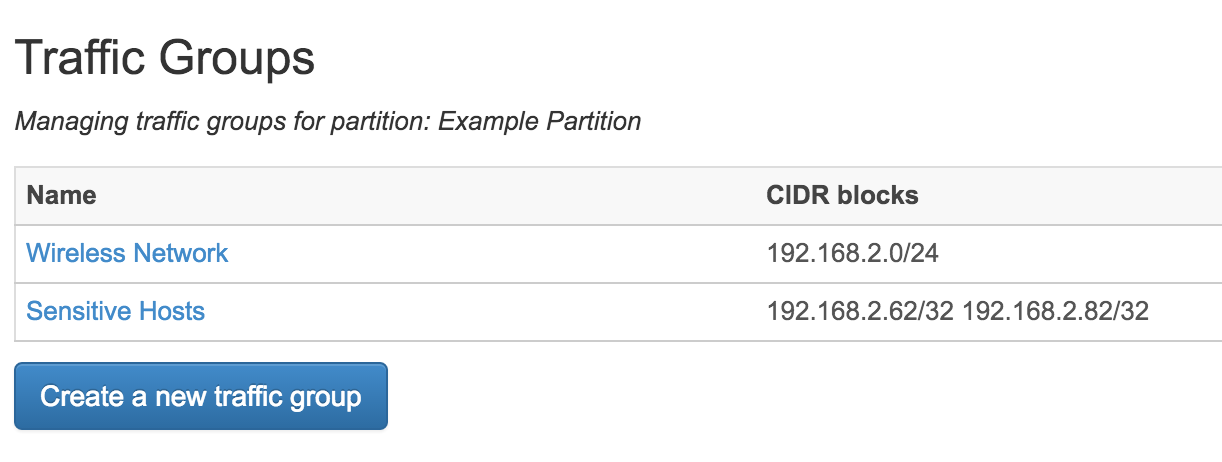
This page gives you an interface to create new Traffic Groups. In the screenshot above, the "Wireless Network" traffic group was defined by simply typing "192.168.2.0/24" into CIDR blocks and IPs box. Hitting space, enter, or a comma between blocks or IPs, or clicking outside the entry box, triggers FlowTraq to check the address you entered for validity. (Validated IPs/blocks can be removed by the 'x' in the corner of the gray box in which they appear) Lists of blocks and IPs can be pasted in from a file where they are delimited by commas and/or whitespace.
Press the "Save Traffic Group" to save the definition. From this point forward, any new flow that arrives will be tagged according to the new definition. Ongoing sessions (such as long-running downloads) or sessions that have already finished will not be affected.
As noted earlier, Traffic Group definitions are made on a "most specific match" basis. In the case given here, the CIDR block 192.168.2.0/24 is a subset of the 192.168.0.0/16 block already defined in the RFC 1918 Traffic Group. If a flow arrives involving host 192.168.2.62, it will be annotated as belonging to "Wireless Network", because 192.168.2.0/24 is a more specific definition than 192.168.0.0/16.
Port/Protocol is a further way of refining Traffic Group membership, and is applied after IP/CIDR matching. This refinement is most often used in the case where an IP address or netblock may refer to a different host depending on the port used.
![[Note]](../common/images/admon/note.png) | Note |
|---|---|
It is usually not necessary to define Traffic Groups by port/protocol pair. Alerting based on port/protocol threshold can be performed on all Traffic Groups. |
In most cases, overlap will be kept to a minimum, but it is occasionally useful to be able to describe subset netblocks or even individual IPs to separate blocks. To help understand assignment in these cases, it may be useful to examine a few examples. In the following, three traffic groups are defined:
In the communication 192.168.1.100:45678 → 8.8.8.8:53 (UDP), the first host belongs to the "RFC 1918" Traffic Group, and the second host does not belong to any groups currently defined. The annotation becomes, 192.168.1.100:45678 ["RFC 1918"] → 8.8.8.8:53 [] (UDP)
In the communication 192.168.2.100:45678 → 192.168.1.101:22 (TCP), both IPs match the IP rule for "RFC 1918", but the first host matches the more-specific IP rule for "Wireless Network", and so the annotation becomes, 192.168.2.100:45678 ["Wireless Network"] → 192.168.1.101:22 ["RFC 1918"] (TCP)
In the communication 192.168.1.100:45678 → 192.168.1.101:80 (TCP), both addresses match the IP rule for "RFC 1918", but the second host matches the IP rule and port rule for "Web Servers", and so the annotation becomes, 192.168.1.100:45678 ["RFC 1918"] → 192.168.1.101:80 ["Web Servers"] (TCP)
In the communication 192.168.1.100:45678 → 192.168.2.10:80 (TCP), both addresses match the IP rule for "RFC 1918", but the second host matches two more specific rules: the IP rule for "Wireless Network" (192.168.2.0/24) and the IP rule and port rule for "Web Servers" (192.168.0.0/16 and TCP/80). The Wireless Network IP rule is more specific, and so takes precedence. The annotation becomes, 192.168.1.100:45678 ["RFC 1918"] → 192.168.2.10:80 ["Wireless Network"] (TCP)
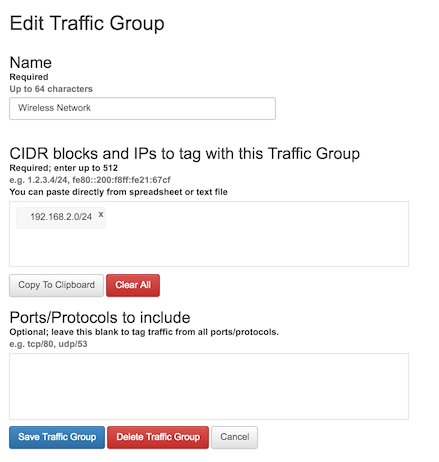
To delete a Traffic Group, navigate to the Traffic Group page, select the associated Partition (if more than one Partition is available) and click on the name of the group in blue. At the bottom of the editing page is a red button to delete the selected group.
Traffic Groups cannot be undeleted, however their information persists in FlowTraq. All historical flows that had previously been defined with a now-deleted Traffic Group will continue to show that original name, and trend data on the Quickviews page for that Traffic Group will remain available. It is not possible to recycle the Traffic Group's internal ID number, although the name and CIDR list can be re-used (a different ID will be assigned).
Once Traffic Groups have been created, FlowTraq begins keeping long term histories on their traffic patterns. Only summaries are stored for this feature, and are described in terms of:
Bit rate into the group
Bit rate out of the group
Packet rate into the group
Packet rate out of the group
New connection rate (in and out)
Flow update rate
These rates are all calculated on a minute-by-minute basis. "In" and "Out" are defined according to the Traffic Group itself. A transfer of data from one Traffic Group on your network to another one will be tallied in the "Out" history for the first group, and the "In" for the second.
In addition to broad Traffic Group-level statistics, FlowTraq keeps statistics on the top hosts, and port/protocol combinations, compiling minute-by-minute summaries. For each of these items, the same tallies are kept (e.g. bit rate in, bit rate out, etc).
Finally, for each host in the top list in each summary period, statistics are kept for it:
Local Port/Protocol - The port/protocols to and from which data is sent on that host. If the host is a web server, for example, this may include TCP/80 and TCP/443, as determined by the applications used. If the host is a user laptop making only outbound connections, by contrast, the top local ports may be dominated by ephemeral ports.
Remote Port/Protocol - The port/protocol combinations to which this host is sending data. If the host is a user's workstation, this may likely include TCP/80, UDP/53 and similar applications. If the host receives only inbound connections, these may be dominated by ephemeral ports.
Local Endpoints - The top service endpoints within the partition (included in any Traffic Group in that partition) with which this host communicated; e.g. local mail or file servers.
Remote Netblocks - The top netblocks (outside the Traffic Groups in this partition) with which this host communicated
For each of these divisions and subdivisions, the same rates (bit rate in, bit rate out, packet rate in, etc) are recorded.